This post is kind of a continuation of a previous post of mine, Fun with Wireshark and AIM. The challenge this time is to determine the following from a .pcap file:
1. What is Ann’s email address?
2. What is Ann’s email password?
3. What is Ann’s secret lover’s email address?
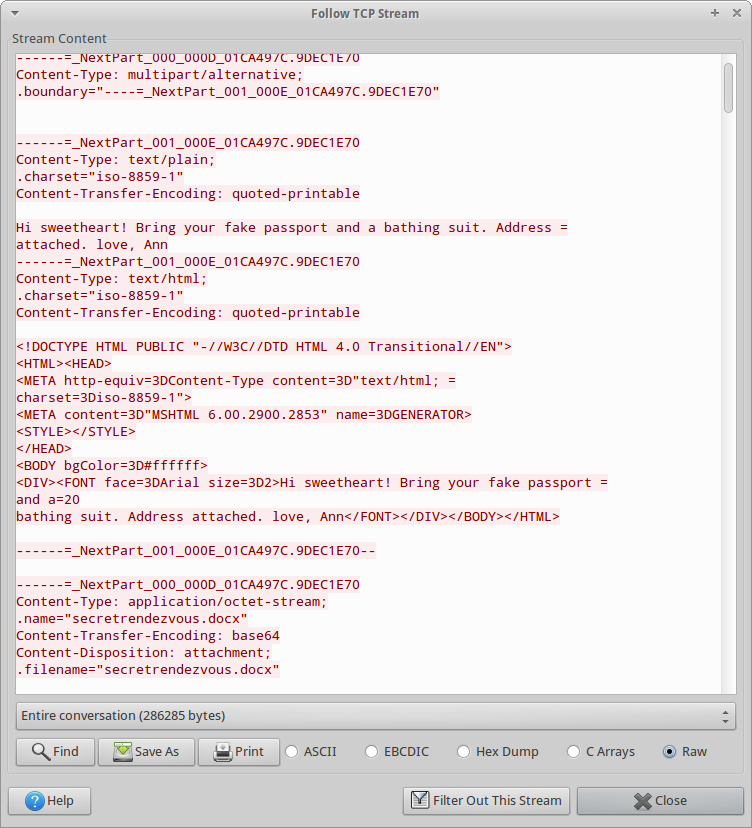
4. What two items did Ann tell her secret lover to bring?
5. What is the NAME of the attachment Ann sent to her secret lover?
6. What is the MD5sum of the attachment Ann sent to her secret lover?
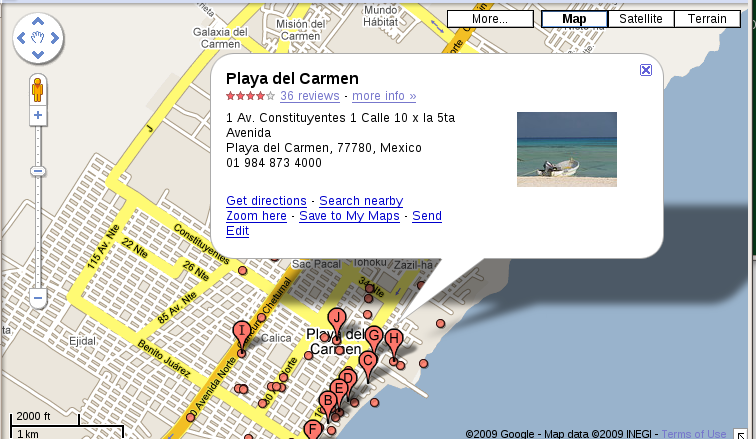
7. In what CITY and COUNTRY is their rendez-vous point?
8. What is the MD5sum of the image embedded in the document?
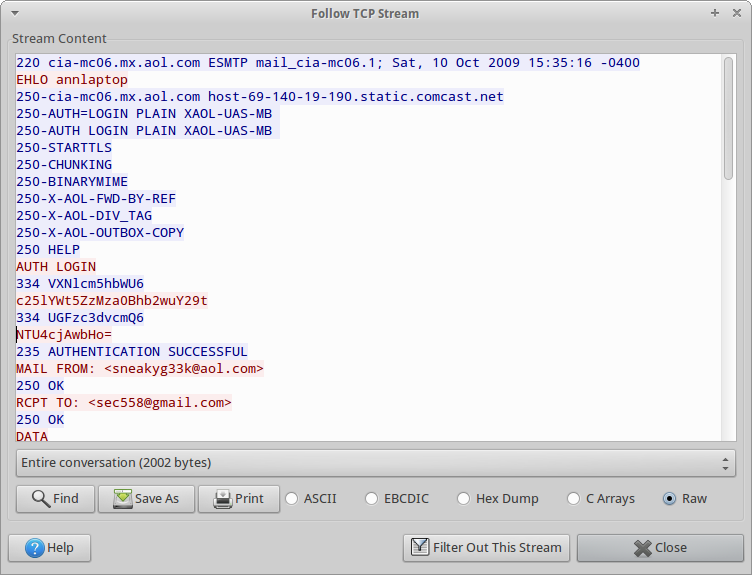
Opening up the pcap file with Wireshark, it’s obvious that Ann is using unencrypted SMTP. If we follow the TCP stream, we see the following:
Commands sent from Ann are in red, responses from the server are in blue. We can see that Ann sent an AUTH LOGIN command to the server, followed by some text that is not human readable. Reading up on the AUTH LOGIN command, we can see that the username and password aren’t actually encrypted, just encoded using base64. Decoding them reveals that Ann’s username is sneakyg33k@aol.com with a password of 558r00lz.
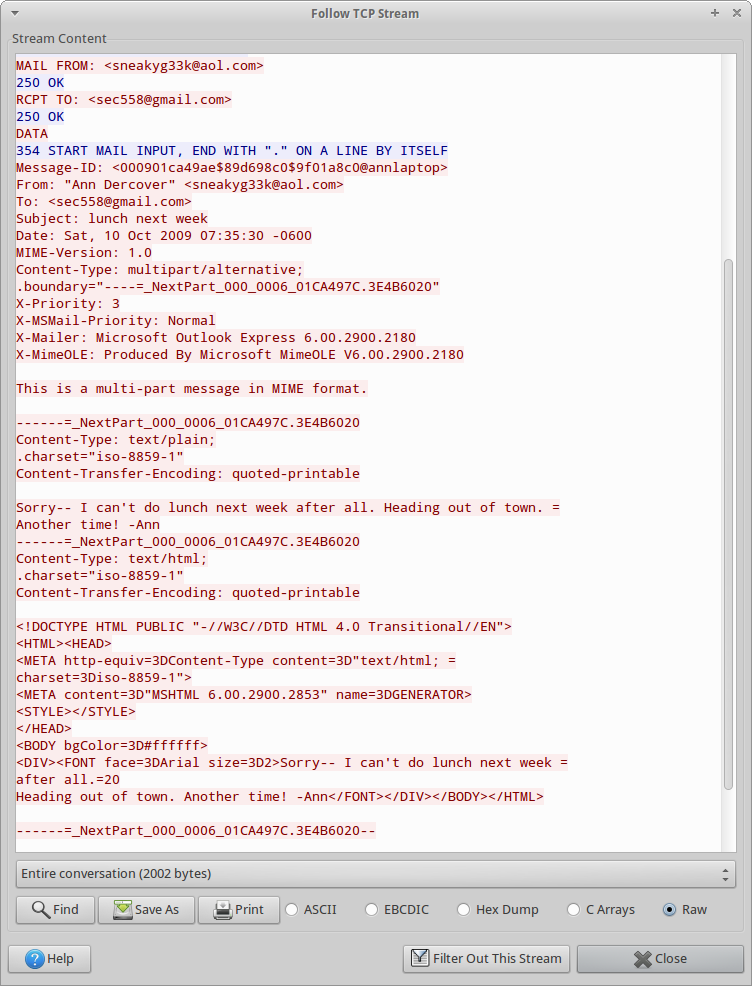
The recipient of the email can be determined by looking at the RCPT TO field, which is also in plain text (sec558@gmail.com). In addition, we can see the first part of this multi-part message:
To see the second part of this multipart message, I just incremented the tcp.stream from 2 to 3, which gives us the answers to questions 4 and 5:
Now we need to somehow extract this message from the email. The approach we used for challenge #1 should work here: save the stream to disk, remove the parts we don’t actually need, and try to open the attachment.
Step 1 is the same as it was in challenge 1: save the stream to disk. Next, we need to remove all the data that isn’t actually part of the attachment. I did this manually through vim, although I’m sure there’s a better way. Next, I whipped up a little python script that:
- Reads in the base64-encoded attachment, line-by-line
- Strips off the newline
- Writes the decoded data to decoded.bin
#!/usr/bin/python
import base64
fin = open("attachment.txt", 'r')
fout = open("decoded.bin", 'wb')
for line in fin:
encoded_data = line.rstrip()
decoded_data = base64.b64decode(encoded_data)
fout.write(decoded_data);
fin.close()
fout.close()
The script worked as intended. Opening up the file, we see that it has a magic number of 50 4b 03 04 14 00 06 00″, which is a docx file. We can analyze this file the same way I did for the previous challenge:
jsaxton@stalin:/data/pcap_dumps/contest02$ unzip decoded.bin -d tmp
Archive: decoded.bin
inflating: tmp/[Content_Types].xml
inflating: tmp/_rels/.rels
inflating: tmp/word/_rels/document.xml.rels
inflating: tmp/word/document.xml
extracting: tmp/word/media/image1.png
inflating: tmp/word/theme/theme1.xml
inflating: tmp/word/settings.xml
inflating: tmp/word/webSettings.xml
inflating: tmp/word/styles.xml
inflating: tmp/docProps/core.xml
inflating: tmp/word/numbering.xml
inflating: tmp/word/fontTable.xml
inflating: tmp/docProps/app.xml
jsaxton@stalin:/data/pcap_dumps/contest02$ md5sum tmp/word/media/image1.png
aadeace50997b1ba24b09ac2ef1940b7 tmp/word/media/image1.png
jsaxton@stalin:/data/pcap_dumps/contest02$ sed -e 's/<[^>]*>//g' tmp/word/document.xml
Meet me at the fountain near the rendezvous point. Address below. I’m bringing all the cash.
The address is not in the text above — it is in the the image embedded in the Word document:
 Blog
Blog